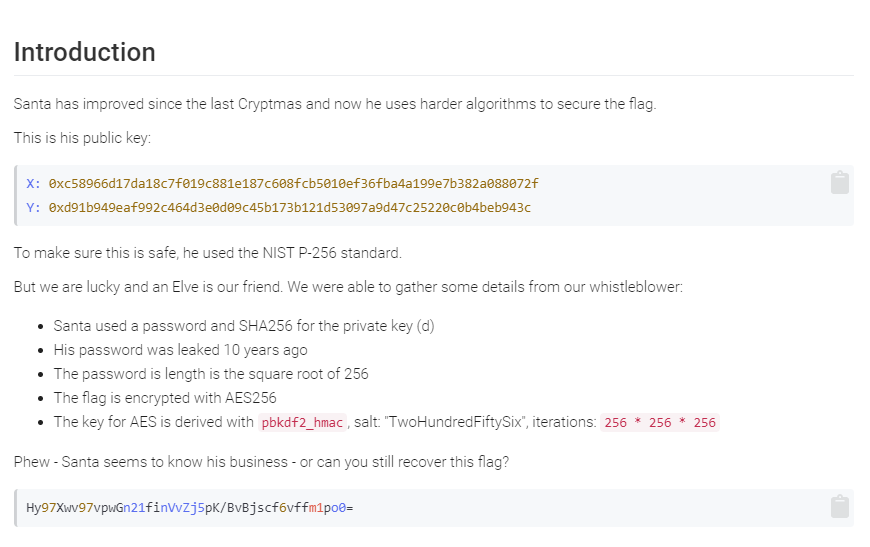
The information provided was pretty helpful. Ten years ago (2009) there was a big password leak, known as rockyou. As his password is 16 characters long we have to check every 16 characters password from the rockyou wordlist. As santa uses NIST-P256 with the SHA256 hash of the password as key, we can simply hash each 16 char pw, calculate the public key and check if it matches the given public key. If so, we then can use pbkdf2_hmac to derive the key used for AES. After that we simply have to decrypt the encrypted flag. I created the following python script which does the job.
import base64
import hashlib
from fastecdsa import keys, curve
from Crypto.Cipher import AES
from Crypto import Random
import binascii
X = 0xc58966d17da18c7f019c881e187c608fcb5010ef36fba4a199e7b382a088072f
Y = 0xd91b949eaf992c464d3e0d09c45b173b121d53097a9d47c25220c0b4beb943c
with open('rockyou.txt', 'r') as file:
while True:
pw = file.readline().strip()
if not len(pw) == 16:
continue
elif not pw:
break
key = hashlib.sha256(pw.encode())
pub = keys.get_public_key(int(binascii.hexlify(key.digest()), 16), curve.P256)
if pub.x == X and pub.y == Y:
print("found pw:", pw)
dk = hashlib.pbkdf2_hmac('sha256', pw.encode(), b'TwoHundredFiftySix', 256**3)
print(dk.hex())
cipher = AES.new(dk, AES.MODE_ECB)
print(cipher.decrypt(base64.b64decode('Hy97Xwv97vpwGn21finVvZj5pK/BvBjscf6vffm1po0=')).decode())
break
This gives us the flag: HV19{sry_n0_crypt0mat_th1s_year}.