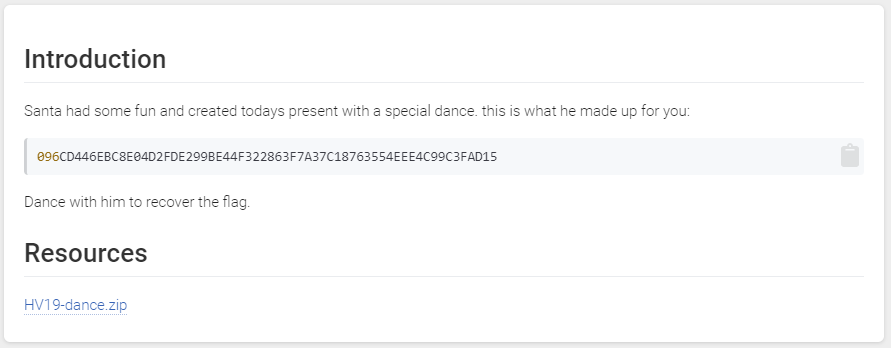
The attached zip file contained a binary called dance which is an actual iOS binary. It will ask you for some input and will return the flag.
After looking at the crypto implementation I thought that this could be the Salsa20 cipher – which would also fit the name. Analysing the main function and the parameters used to call the dance function got me the following python script which can be used to get the flag.
import binascii, hashlib
from salsa20 import *
keys = [
"0320634661B63CAFAA76C27EEA00B59B0320634661B63CAFAA76C27EEA00B59B",
"0320634661B63CAFAA76C27EEA00B59BFB2F7097214FD04CB257AC2904EFEE46",
"0320634661B63CAFAA76C27EEA00B59B79730FF4EC0C406BFD91C91FE70400A8",
"0320634661B63CAFAA76C27EEA00B59BADF16C63456A5EF1ED9D79469DA2A0B5",
"FB2F7097214FD04CB257AC2904EFEE46FB2F7097214FD04CB257AC2904EFEE46",
"FB2F7097214FD04CB257AC2904EFEE460320634661B63CAFAA76C27EEA00B59B",
"FB2F7097214FD04CB257AC2904EFEE4679730FF4EC0C406BFD91C91FE70400A8",
"FB2F7097214FD04CB257AC2904EFEE46ADF16C63456A5EF1ED9D79469DA2A0B5",
"79730FF4EC0C406BFD91C91FE70400A879730FF4EC0C406BFD91C91FE70400A8",
"79730FF4EC0C406BFD91C91FE70400A80320634661B63CAFAA76C27EEA00B59B",
"79730FF4EC0C406BFD91C91FE70400A8FB2F7097214FD04CB257AC2904EFEE46",
"79730FF4EC0C406BFD91C91FE70400A8ADF16C63456A5EF1ED9D79469DA2A0B5",
"ADF16C63456A5EF1ED9D79469DA2A0B5ADF16C63456A5EF1ED9D79469DA2A0B5",
"ADF16C63456A5EF1ED9D79469DA2A0B50320634661B63CAFAA76C27EEA00B59B",
"ADF16C63456A5EF1ED9D79469DA2A0B5FB2F7097214FD04CB257AC2904EFEE46",
"ADF16C63456A5EF1ED9D79469DA2A0B579730FF4EC0C406BFD91C91FE70400A8",
]
messages = [
binascii.unhexlify("096CD446EBC8E04D2FDE299BE44F322863F7A37C18763554EEE4C99C3FAD15"),
"096CD446EBC8E04D2FDE299BE44F322863F7A37C18763554EEE4C99C3FAD15"
]
nonces = [
"b132d0a8e78f4511",
"e78f4511b132d0a8",
"7ef854111b230d8a",
"1b230d8a7ef85411",
"b132d0a8e78f4511"[::-1],
"e78f4511b132d0a8"[::-1],
"7ef854111b230d8a"[::-1],
"1b230d8a7ef85411"[::-1]
]
for key in keys:
for message in messages:
for nonce in nonces:
output = Salsa20_xor(message, binascii.unhexlify(nonce), binascii.unhexlify(key))
if "HV19" in output:
print(key)
print(nonce)
print(output)
Running it reveals HV19{Danc1ng_Salsa_in_ass3mbly}.