The attached file turned out to be an intel hex file containing some kind of an arduino program or something. Loading the file in ghidra and poking around showed some methods which seem to just swap around variables.
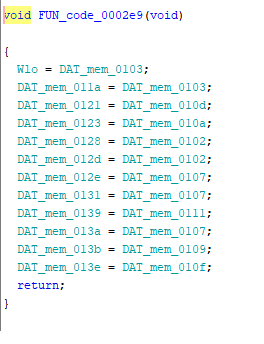
I recreated this behaviour in python and got the flag.
data = [c for c in "0139HSV_acdghlmnrtxy{}"]
for i in range(0, 0x58 - len(data)): data.append('')
offsets = [ [0x02, 0x34], [0x14, 0x1b], [0x11, 0x2a], [0x02, 0x25], [0x00, 0x3c], [0x02, 0x22], [0x13, 0x1e], [0x12, 0x38], [0x10, 0x3d], [0x02, 0x2d], [0x02, 0x28], [0x11, 0x39], [0x0f, 0x3e], [0x09, 0x3b], [0x07, 0x3a], [0x0d, 0x21], [0x07, 0x31], [0x07, 0x2e], [0x0a, 0x23], [0x03, 0x1a], [0x02, 0x3f], [0x06, 0x18], [0x10, 0x40], [0x0b, 0x24], [0x0e, 0x27], [0x08, 0x2f], [0x15, 0x41], [0x11, 0x30], [0x07, 0x1f], [0x02, 0x37], [0x0f, 0x36], [0x02, 0x29], [0x0e, 0x2c], [0x07, 0x26], [0x04, 0x1c], [0x01, 0x19], [0x07, 0x35], [0x04, 0x17], [0x05, 0x20], [0x0c, 0x33], [0x07, 0x2b], [0x02, 0x1d], [0x11, 0x32] ]
for i in offsets:
src, dst = i[0], i[1]
data[dst] = data[src]
print("".join(data))
The flag is HV19{H3y_Sl3dg3_m33t_m3_at_th3_n3xt_c0rn3r}.